
New iProxy features: remote connection switching, proxy prefix, proxy access format, and remote app update.
Knowledge Base
Evgeny Fomenko2025-06-13
4
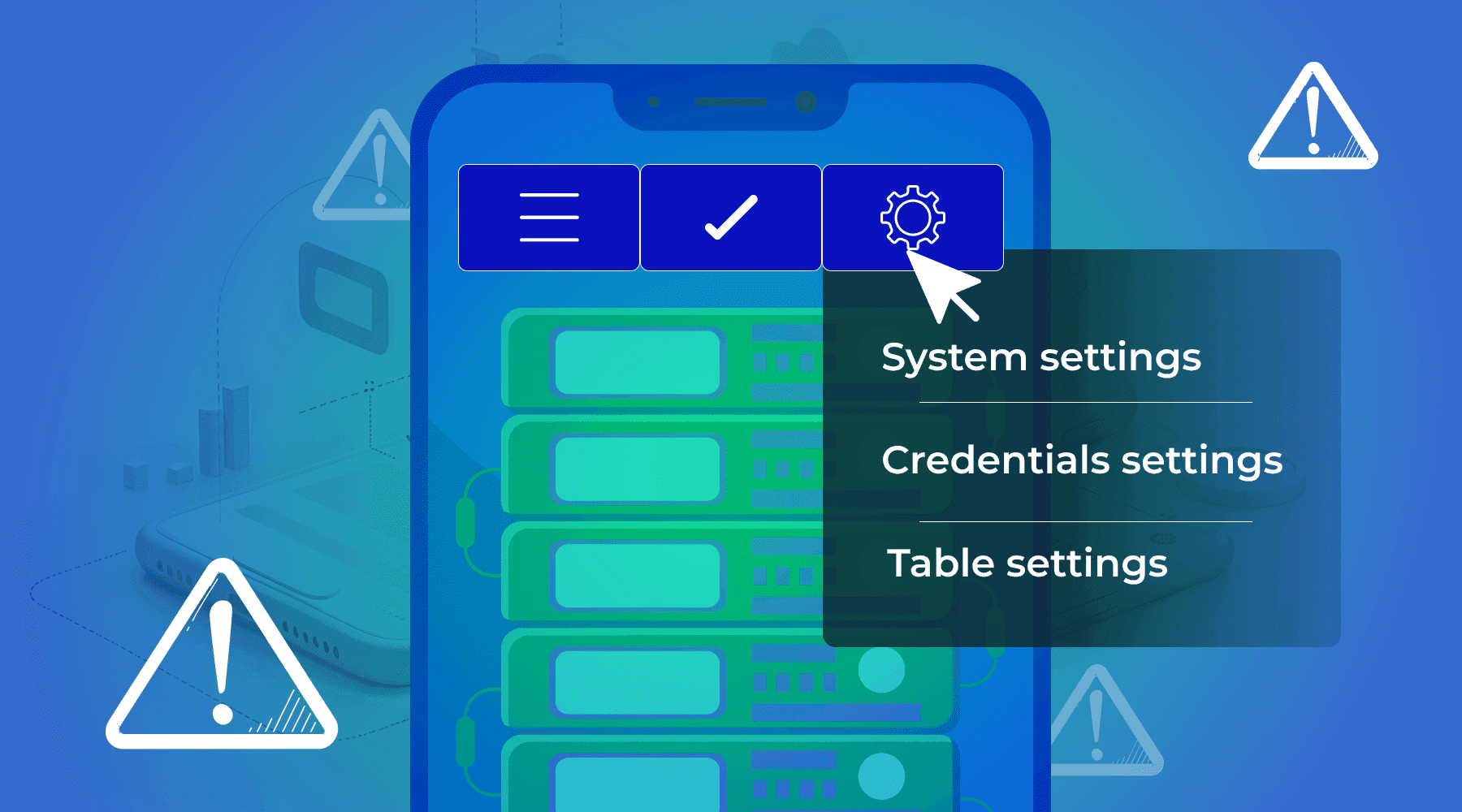
In this article, we will explain how to set up a custom dashboard in your personal account to make working with proxies as clear, convenient, and fast as possible.
Getting Started
Maria Devi2025-05-28
5

Compare the 10 best proxy providers by pricing, features, and performance. Discover how iProxy stands out with DIY mobile proxies for maximum control, affordability, and anonymity.
Knowledge Base
Evgeny Fomenko2025-05-07
10

Discover Push.Express — the ultimate tool to boost user engagement, retention, and ROI with automated push notifications for web, Android, iOS, and PWA.
Reviews
Evgeny Fomenko2025-04-09
4

Learn how to build a profitable mobile proxy farm from scratch. Expert advice, startup costs, device tips, and real insights from a trusted U.S. iProxy seller — all in one guide.
Proxy Farming
Evgeny Fomenko2025-04-06
5

- Best Mobile Proxy Providers [2025]
- How to Set Up Remote Change of IP Address Through iProxy.online?
- How to Make Money With Proxies [The Complete Guide]
- How to Increase the Proxy Speed: Detailed Guide
- Guide for setting up mobile proxies in iProxy.online
- All about .OVPN configs, UDP, HTTP/3, QUIQ support
- What is Wi-Fi Split? How does it help to increase the speed and reduce traffic consumption?
- Replace passive OS fingerprint in mobile proxies
- List of recommended phones for iProxy.online
- How to choose the right location of the server?